
Aurich Lawson | Getty Images
Over the past year, a new term has emerged to describe an online scam that brings in millions or even billions of dollars a year. It’s called “pig butchering,” and now even Apple is getting tricked into participating.
Researchers from security firm Sophos said on Wednesday they discovered two apps available on the App Store that were part of an elaborate network of tools used to trick people into investing large sums of money in fake investment scams. At least one of these apps has also been integrated into Google Play, but this market is notorious for the number of malicious apps that circumvent Google’s control. Sophos said it was the first time it had seen such apps in the App Store and that a previous app identified in these types of scams was a legitimate app that was later exploited by bad actors.
Hog Slaughter relies on a rich combination of apps, websites, web hosts, and humans – in some cases victims of human trafficking – to build trust with a brand over a period of time. weeks or months, often under the guise of a romantic interest, financial advisor, or successful investor. Eventually, the online discussion will turn to investments, usually involving cryptocurrency, which the scammer claims to have earned huge sums of money from. The scammer then invites the victim to participate.
Once a brand deposits money, the scammers initially allow them to make withdrawals. The scammers end up locking the account and claiming that they need a deposit of up to 20% of their balance to get it back. Even when the deposit is paid, the money is not returned and the scammers come up with new reasons why the victim should send more money. The term pig butcher comes from the fact that a farmer fattens a pig months before it is slaughtered.
Breach of Trust in the App Store
Sophos said it recently found two iOS listings in the App Store that were used for CryptoRom, a type of hog butcher that uses romantic overtures to build trust in its victims. The first was called Ace Pro and claimed to be an app for scanning QR codes.
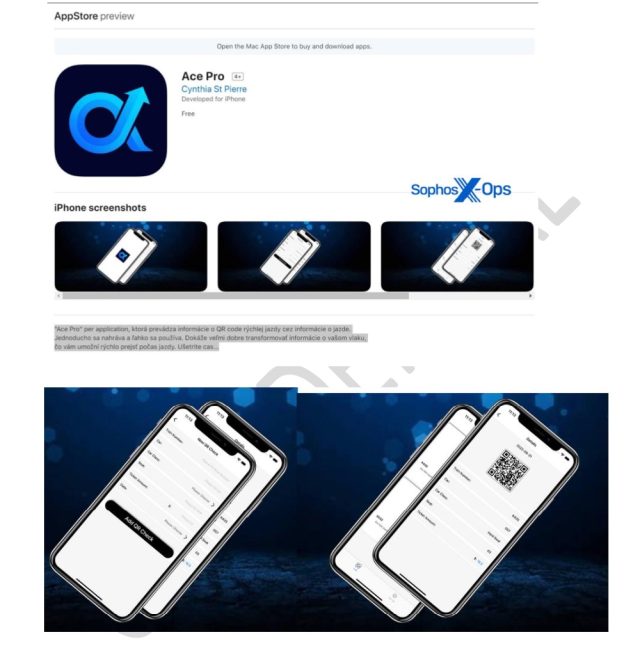
The second app was MBM_BitScan, which advertised itself as a real-time data tracker for cryptocurrencies. A victim Sophos tracked paid around $4,000 into the app before realizing it was fake.

Apple is famous for its reputation, justified or not, for filtering out malicious apps before they end up in the App Store. Combined with detailed fake online profiles and elaborate stories that scammers use to lure victims, the apps’ presence in the App Store made the ruse all the more convincing.
“If criminals can get past these checks, they have the potential to reach millions of devices,” the Sophos researchers wrote. “That’s what makes it more dangerous for CryptoRom victims, because most of those targets are more likely to trust the source if it’s from Apple’s official app store.”
Apple representatives did not respond to an email requesting an interview for this story. Google PR also declined an interview, but said in an email that the company removed the app after receiving a warning from Sophos.
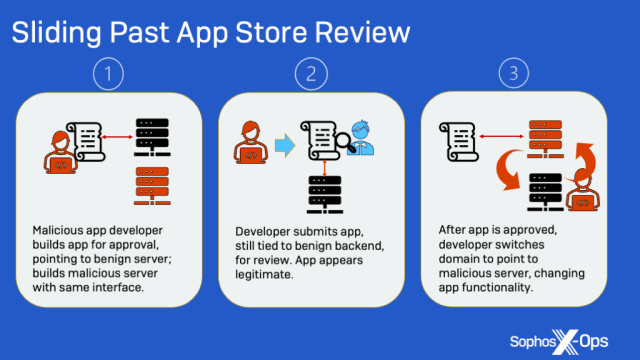
Ace Pro and MBM_BitScan bypassed Apple’s verification process by using remote content downloaded from hard-coded web addresses to deliver their malicious functionality. When Apple reviewed apps, the sites likely provided benign content. Eventually, that changed.
Ace Pro, for example, started sending a request to the domain rest.apizza[.]net, which would then respond with the content from acedealex[.]xyz, which would provide the fake trading interface. MBN_BitScan contacted a server hosted by Amazon, which in turn beckoned flyerbit8[.]com, a domain designed to look like the legitimate Bitcoin service bitFlyer.
The process looked like this:
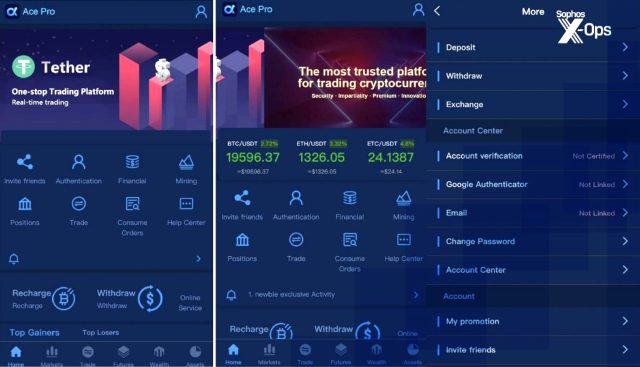
The fake interface gave the appearance of allowing users to deposit and withdraw money and respond to customer service requests in real time. To get the victims started, the scammers asked them to transfer money into the Binance exchange and from there from Binance to the fake app.
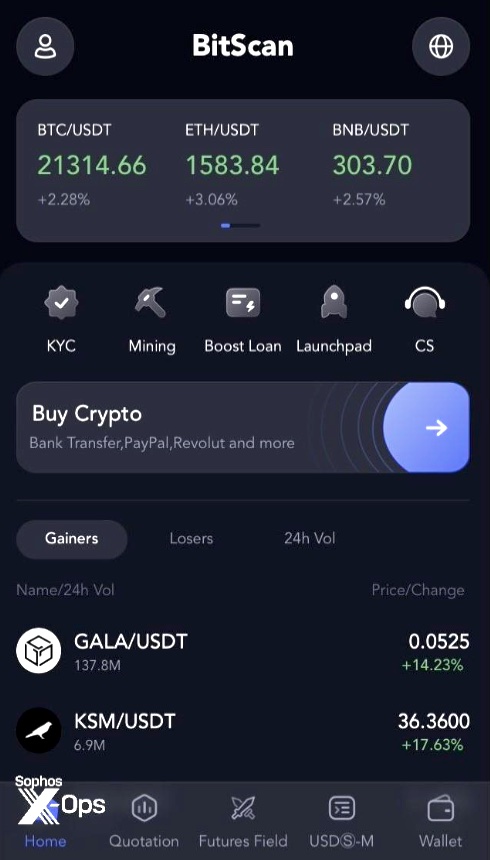
Fake trading interface provided by MBM_BitScan.
